Malicious shortcut generator for collecting NTLM hashes from insecure file shares
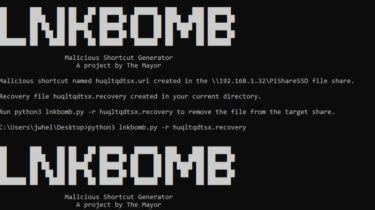
Lnkbomb is used for uploading malicious shortcut files to insecure file shares. The vulnerability exists due to Windows looking for an icon file to associate with the shortcut file. This icon file can be directed to a penetration tester’s machine running Responder or smbserver to gather NTLMv1 or NTLMv2 hashes (depending on configuration of the victim host machine). The tester can then attempt to crack those collected hashes offline with a tool like Hashcat.
The payload file is uploaded directly to the insecure file specified by the tester in the command line. The tester includes their IP address as well, which is written into the payload.
Usage
Installing Lnkbomb
git clone https://github.com/dievus/lnkbomb.git
Change

