Jni Generator module extracted from Chromium project
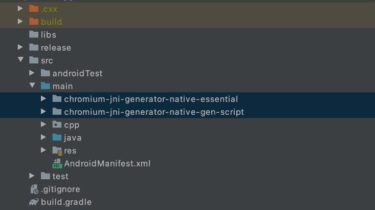
1 Dependencies 1.1 C ++ dependencies Copy two directories: chromium-jni-generator-native-essential and chromium-jni-generator-native-gen-script to your projectThe chromium-jni-generator-neutral-essential directory contains the chromium_jni_generator_native_essential .h and chromium_jni_generator_native_essential.ccThe chromium-jni-generator-native-gen-script directory contains python scripts that generate native codechromium_native_code_gen.sh is an example of using python scripts to generate native code #!/bin/bash #create code generation directories rm -rf ./gen mkdir -p gen/cpp mkdir -p gen/java #generate native code ./jni_generator.py –input_file XXXXA.java –input_file XXXXB.java –output_file gen/cpp/XXXXA.h –output_file gen/cpp/XXXXB.h 1.2 Java dependencies
Read more