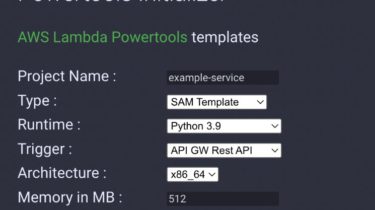
Quickstart site to build out a lambda function
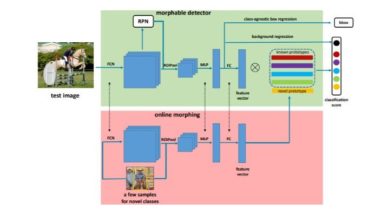
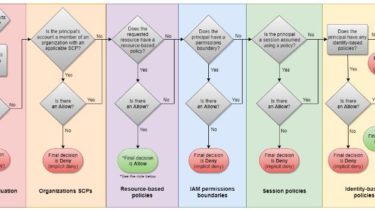
Create a mini Spring initializer for AWS Lambda functions. Backend service Builds a layer for the different cookiecutter templates. (NOTE: This will be limited for what we can bundle) Webservice includes a number of parameters for the aws lambda powertools templates: name: defaults to hello-world, is the name of the project runtime: defaults to python3.9, is the language runtime version (could also support typescript via nodejs) architecture: defaults to x86_64, is the CPU architecture (can also be arm64) memory: defaults […]
Read more