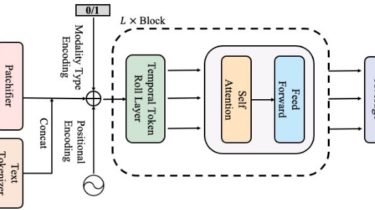
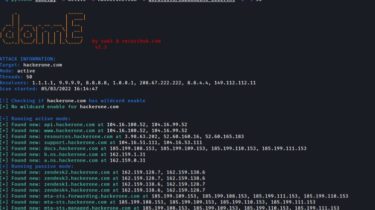
Refine video frame based on nearby frames
Introduction Refine a video frame based on nearby frames. WIP CLI Usage Installation git clone [email protected]:hzwer/ResynNet.git cd ResynNet pip3 install -r requirements.txt Download the pretrained model from here. Unzip and move the pretrained parameters to train_log/* Run python3 inference_img.py –origin example/origin.png –ref example/ref0.png example/ref1.png Sponsor Many thanks to Grisk. 感谢支持 Paypal Sponsor: https://www.paypal.com/paypalme/hzwer GitHub View Github
Read more