Category: Authentication
OAuth Device Code Authorization Phishing Script
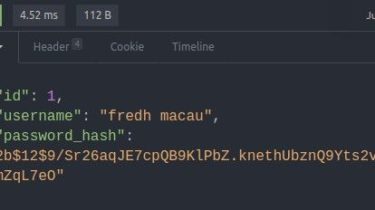
Some scripts to utilise device code authorization for phishing. High level overview as per the instructions as: https://o365blog.com/post/phishing/ An attacker connects to /devicecode endpoint and sends client_id and resource After receiving verification_uri and user_code, create an email containing a link to verification_uri and user_code, and send it to the victim. (delivering the phishing email is not in scope for this project) Victim clicks the link, provides the code and completes the sign in. The attacker receives access_token and refresh_token and […]
Read morePython SDK for accessing the Hanko Authentication API
This package is maintained by Hanko. Introduction This SDK provides an API client that lets you communicate with theHanko Authentication APIto easily integrate FIDO®-based authentication into your web application written inPython. Documentation Installation Pip Building a wheel py -m build pip install dist/hanko_sdk-X.X.X-py3-none-any.whl Usage Prerequisites In order to utilize the client provided by the SDK you need an API URL as well as API credentials in the form of anAPI key ID and an API secret. View our getting […]
Read moreAn open solution for strong two-factor authentication like OTP tokens
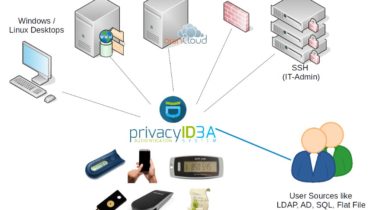
privacyIDEA privacyIDEA is an open solution for strong two-factor authentication like OTP tokens, SMS, smartphones or SSH keys. Using privacyIDEA you can enhance your existing applications like local login (PAM, Windows Credential Provider), VPN, remote access, SSH connections, access to web sites or web portals with a second factor during authentication. Thus boosting the security of your existing applications. Overview privacyIDEA runs as an additional service in your network and you can connect different applications to privacyIDEA. privacyIDEA does not […]
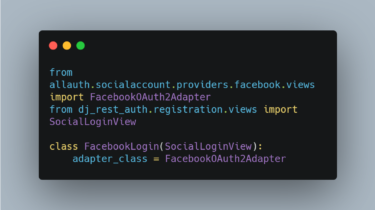
Read moreAuthentication for Django Rest Framework
Dj-Rest-Auth Drop-in API endpoints for handling authentication securely in Django Rest Framework. Works especially well with SPAs (e.g React, Vue, Angular), and Mobile applications. Requirements Quick Setup Install package pip install dj-rest-auth Add dj_rest_auth app to INSTALLED_APPS in your django settings.py: INSTALLED_APPS = ( …, ‘rest_framework’, ‘rest_framework.authtoken’, …, ‘dj_rest_auth’ ) Add URL patterns urlpatterns = [ path(‘dj-rest-auth/’, include(‘dj_rest_auth.urls’)), ] (Optional) Use Http-Only cookies REST_USE_JWT = True JWT_AUTH_COOKIE = ‘jwt-auth’ Testing Install required modules with pip install -r dj_rest_auth/tests/requirements.pip To run […]
Read moreAn authentication bypass on polkit which allows unprivileged user to call privileged methods using DBus
Polkit-exploit – CVE-2021-3560 Privilege escalation with polkit – CVE-2021-3560 CVE-2021-3560 is an authentication bypass on polkit, which allows unprivileged user to call privileged methods using DBus, in this exploit we will call 2 privileged methods provided by accountsservice (CreateUser and SetPassword), which allows us to create a priviliged user then setting a password to it and at the end logging as the created user and then elevate to root. Ahmad Almorabea @almorabea http://almorabea.net [email protected]:~/Desktop$ python3 CVE-2021-3560.py ************** Exploit: Privilege escalation […]
Read more